Warning: Hacked IP Cams & Voyeurism - What You Need To Know
Are your private moments truly private, or are unseen eyes watching? The disturbing reality is that your home security system, your IP camera, might be a portal for unauthorized access, transforming your sanctuary into a stage for voyeurs.
The vulnerability of IP cameras, those ubiquitous eyes safeguarding our homes and businesses, has become a chilling concern. These devices, intended to provide security and peace of mind, can be easily compromised, turning them into tools for malicious actors. The ease with which these systems can be hacked and exploited is alarming, particularly given the sensitive nature of the environments they monitor: bedrooms, living rooms, offices, and even medical facilities. This isn't a hypothetical threat; it's a growing epidemic, fueled by readily available hacking tools and a thriving online market for compromised feeds.
| Category | Information |
|---|---|
| Common Vulnerabilities | Default passwords, outdated firmware, lack of encryption, open ports. |
| Consequences of Hacking | Privacy breaches, stolen data, identity theft, blackmail, physical danger. |
| Platforms Where Exploits are Shared | Telegram, dark web forums, specialized hacking communities. |
| Types of Content Targeted | Live feeds, recorded footage, personal information stored on the device. |
| Commonly Hacked Brands | Hikvision (historically, due to widespread use and past vulnerabilities), generic unbranded cameras. |
| Security Measures | Strong passwords, firmware updates, disabling UPnP, using a VPN, enabling two-factor authentication, segmenting the camera network. |
| Resources for Checking Security | Shodan (search engine for internet-connected devices), manufacturer's security advisories, independent security audits. |
| Legal Repercussions for Hackers | Vary depending on jurisdiction, but can include hefty fines, imprisonment, and civil lawsuits. |
| Cost of Compromised IP camera | Bought a ipcam sharing group for 30. Will send a mega link of it all for 10 (i cant inv to telegram group as im not owner) dm for more. |
For more information on IP camera security and vulnerabilities, please visit: US-CERT
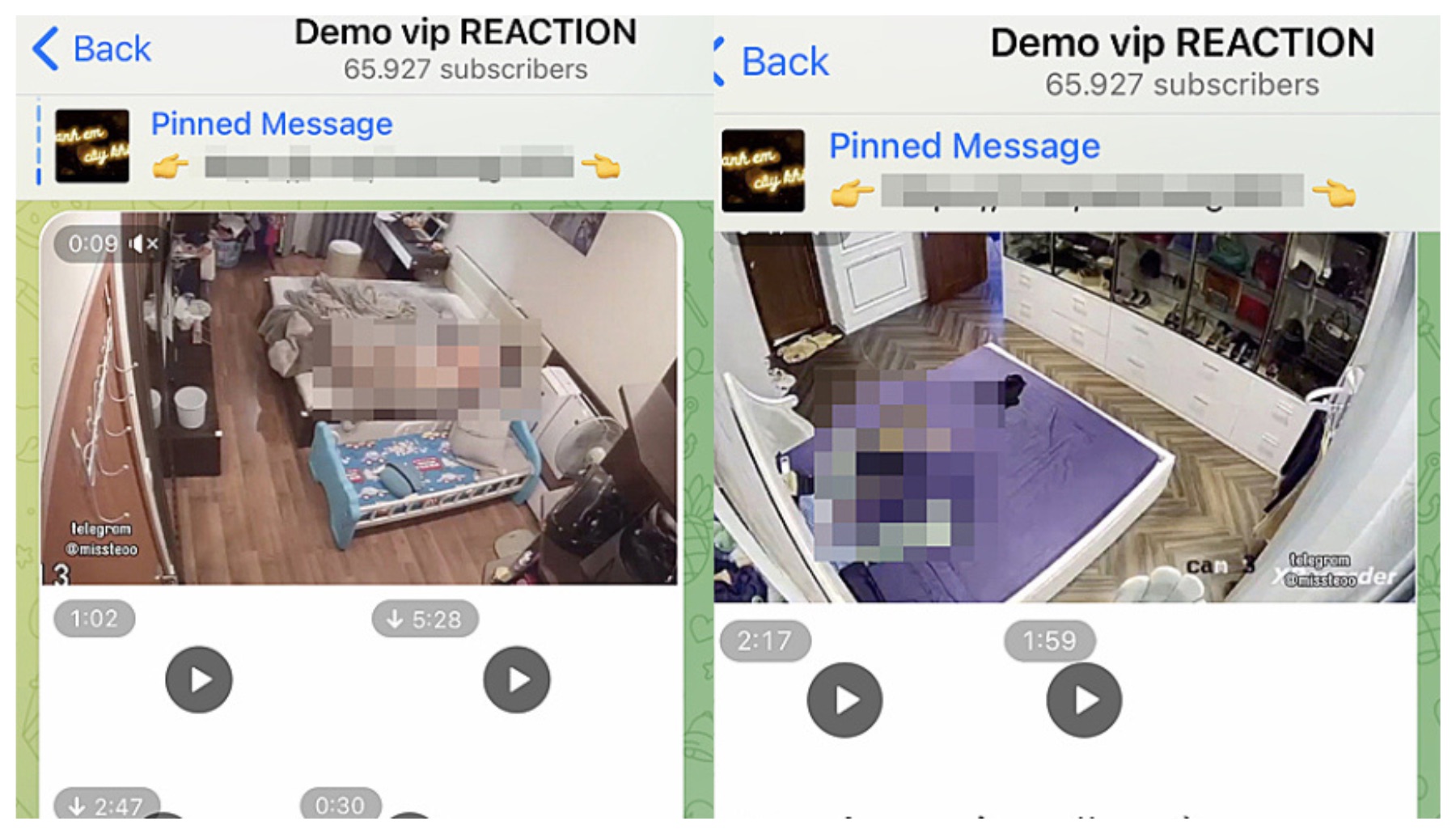
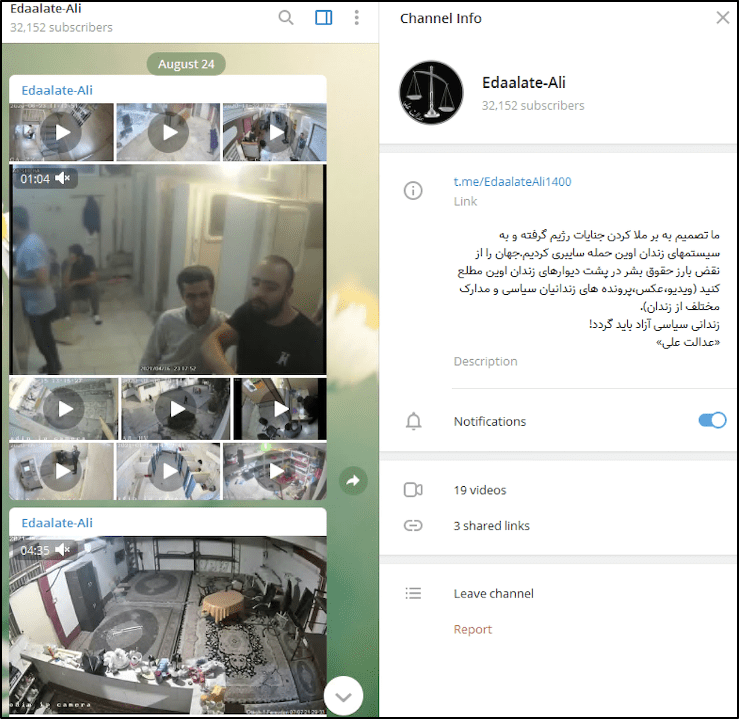
The dark corners of the internet buzz with activity centered around compromised IP cameras. Platforms like Telegram, often lauded for their encrypted messaging, have become havens for the exchange and sale of access to these hacked devices. Groups with thousands of members openly advertise and trade in stolen feeds, offering access to live streams and recorded footage. Disturbingly, some of these channels explicitly target specific types of content, using coded language like "cp" (child pornography), "kids room," "family room," and "bedroom of a young girl" to attract users seeking illicit material. This underscores the depravity of the individuals involved and the grave risks posed to unsuspecting victims.
An investigation by IPVM, a renowned research firm specializing in video surveillance, uncovered a disturbing trend: the blatant sale of access to hacked cameras on Telegram. These sales offers frequently included cameras labeled for family homes, medical offices, salons, and locker rooms, suggesting a deliberate targeting of vulnerable locations. The ease with which these offers were made and the apparent demand for such services highlight the scale of the problem and the urgent need for increased awareness and security measures.
The allure of easy money and the anonymity afforded by the internet have created a fertile ground for this type of cybercrime. Hackers exploit vulnerabilities in IP cameras, often stemming from weak passwords, outdated firmware, or misconfigured network settings. Once they gain access, they can remotely control the camera, view the live feed, and even download recorded footage. This stolen content is then monetized through various means, including direct sales, subscription services, and blackmail. The victims, often unaware of the intrusion, remain vulnerable to further exploitation and potential harm.
- Cory Booker Marriage Plans Rosario Dawson Gay Rumors Facts
- Eazye Compton Legend Born Gone Too Soon 19641995
The implications of a compromised IP camera extend far beyond a simple privacy breach. Stolen footage can be used for identity theft, financial fraud, and even physical harm. Imagine a scenario where a hacker gains access to your home security system and uses it to monitor your movements, learn your routines, and identify valuable possessions. This information could then be used to plan a burglary or even a more violent attack. The psychological impact of knowing that you have been spied on and your privacy violated can be devastating, leading to anxiety, fear, and a loss of trust in technology.
The problem is further exacerbated by the widespread availability of cheap, unbranded IP cameras. These devices, often manufactured with little regard for security, are particularly vulnerable to hacking. They frequently come with default passwords that are easily found online, and they may lack the necessary security features to protect against common attacks. While established brands like Hikvision have faced their own security challenges, they generally invest more in security research and development, and they are more likely to release firmware updates to address vulnerabilities.
The risk isn't limited to just video feeds. Many modern IP cameras come equipped with microphones, allowing hackers to eavesdrop on conversations and gather even more personal information. This audio data can be used to identify individuals, learn about their relationships, and even gather sensitive financial information. The combination of video and audio surveillance creates a highly intrusive and potentially dangerous situation for victims.
One of the key challenges in addressing this issue is the lack of awareness among consumers. Many people simply assume that their IP cameras are secure, without taking the necessary steps to protect them. They may use weak passwords, fail to update firmware, or leave default settings unchanged. This complacency creates an open door for hackers to exploit vulnerabilities and gain unauthorized access.
Another challenge is the complexity of network security. Many IP cameras are connected to home networks that are themselves vulnerable to attack. A compromised router, for example, can provide hackers with access to all devices on the network, including IP cameras. Securing a home network requires a basic understanding of network security principles, including the use of strong passwords, firewalls, and VPNs (Virtual Private Networks).
The issue isn't confined to residential settings. Businesses, medical offices, and other organizations that use IP cameras are also at risk. In fact, these organizations may be even more vulnerable, as they often have a larger number of cameras and a more complex network infrastructure. A security breach in a business setting can lead to the theft of sensitive data, damage to reputation, and financial losses.
The problem is also global in scope. Hackers from all over the world are targeting IP cameras, and the victims are located in every corner of the globe. This makes it difficult to track down and prosecute the perpetrators. International cooperation is essential to combat this type of cybercrime.
What can be done to protect yourself from IP camera hacking? The first and most important step is to change the default password. Use a strong, unique password that is difficult to guess. Avoid using personal information like your name or birthday, and make sure to include a combination of uppercase and lowercase letters, numbers, and symbols.
The next step is to update the firmware regularly. Firmware updates often include security patches that address known vulnerabilities. Check the manufacturer's website for updates, and install them as soon as they become available.
Another important security measure is to disable UPnP (Universal Plug and Play) on your router. UPnP is a protocol that allows devices on your network to automatically configure themselves. While convenient, it can also create security vulnerabilities. Disabling UPnP can help to prevent hackers from gaining access to your IP cameras.
Consider using a VPN (Virtual Private Network) to encrypt your internet traffic. A VPN can help to protect your privacy and prevent hackers from intercepting your data. There are many VPN providers to choose from, so do your research and select one that is reputable and reliable.
Segmenting your network can also improve security. This involves creating separate networks for different types of devices. For example, you could create a separate network for your IP cameras, your computers, and your smart home devices. This can help to prevent a security breach in one part of your network from spreading to other parts.
Be cautious about clicking on suspicious links or downloading files from untrusted sources. These links and files may contain malware that can compromise your IP cameras. Only download files from reputable sources, and always scan them with a virus scanner before opening them.
Regularly monitor your IP camera's activity. Look for any signs of unauthorized access, such as unusual login attempts or changes to settings. If you suspect that your camera has been hacked, disconnect it from the network immediately and contact a security professional.
Be aware of the physical security of your IP cameras. Make sure that they are mounted securely and that they cannot be easily tampered with. Consider using tamper-proof enclosures to protect your cameras from physical attacks.
Educate yourself about IP camera security. The more you know about the risks and vulnerabilities, the better equipped you will be to protect yourself. Read articles, watch videos, and attend workshops on IP camera security.
Remember that security is an ongoing process, not a one-time event. Stay vigilant and keep up with the latest security threats and vulnerabilities. By taking these steps, you can significantly reduce the risk of your IP cameras being hacked and protect your privacy and security.
The information circulating on platforms like Telegram paints a grim picture. Messages such as "You can contact @ipcam right away," "You are invited to a group chat on Telegram," and advertisements for "spy hacked cam" groups with thousands of subscribers are indicative of a thriving underground market for compromised IP camera feeds. The phrase "Link title description memb rating msg qlt online created ms mms pl in;" likely refers to data scraped from these illicit marketplaces, outlining the details of available feeds and their quality.
The claim that "Ip cam talk is a place to discuss ip cameras, cctv, home automation, security, blue iris & everything related" may be a legitimate forum, but it also highlights the inherent risk of discussing sensitive security information online. Even seemingly innocuous discussions can provide hackers with valuable insights into vulnerabilities and potential targets.
The messages "Bought a ipcam sharing group for 30" and "Will send a mega link of it all for 10 (i cant inv to telegram group as im not owner) dm for more" are clear evidence of the commercialization of IP camera hacking. These offers suggest that individuals are profiting from the exploitation of vulnerable devices and the distribution of stolen content.
The alert that "This media is not supported in your browser" is a common occurrence when attempting to view video content from compromised IP cameras. This is often due to the use of proprietary video codecs or streaming protocols that are not supported by standard web browsers.
The sheer scale of the problem is underscored by the statement that "The number of Hikvision cameras that have been hacked in some way are certainly far greater, since this map only shows ip cameras that have not been fixed by December 2017." This suggests that the vast majority of vulnerable devices remain unpatched and susceptible to attack, even years after the initial disclosure of the vulnerabilities.
The timeline of hacking reports, peaking in October and November following the September disclosure, highlights the importance of timely security updates. Users who failed to take action within the month following the disclosure remained vulnerable to exploitation.
The presence of amateur content being advertised ("\ud83d\udd1e new amateur content every day!" and "\u0421\u0432\u0435\u0436\u0438\u0435 \u043b\u044e\u0431\u0438\u0442\u0435\u043b\u044c\u043a\u0438\u0435 \u0444\u043e\u0442\u043e \u043a\u0430\u0436\u0434\u044b\u0439 \u0434\u0435\u043d\u044c!") further underscores the potential for IP cameras to be used for illicit purposes.
The discussion of dynamic IP addresses ("If the router's ip address stays constant, we could stop right now and the ip cam project finished. However, the ip address is assigned by the isp and does not stay the same. We need a way to communicate the most current ip address. The usual way to do this is to get a domain name, and use a dynamic domain name service (ddns) to keep the ip") reveals the technical challenges involved in maintaining remote access to IP cameras. Hackers often use dynamic DNS services to track down vulnerable devices, even if their IP addresses change.
The search terms like "Spy ip cams / voyeur \ud83d\udd1e" and "\u062a\u062c\u0633\u0633 \u062e\u0644\u064a\u062c\u064a \u0639\u0631\u0628\u064a \u0643\u0627\u0645\u064a\u0631\u0627\u062a \u0645\u0631\u0627\u0642\u0628\u0629" (which translates to "Arabian Gulf spying cameras") demonstrate the global demand for voyeuristic content and the diverse range of targets being sought by hackers.
The existence of a subreddit for improperly secured IP cameras ("A subreddit for improperly secured ip cameras") highlights the community that has formed around this issue. While some members may be seeking to raise awareness and offer solutions, others may be exploiting the subreddit for malicious purposes.
The fact that a group chat exists with the name "nh\u00f3m hack camera" is another clear indication of the brazen nature of IP camera hacking. The name itself leaves little doubt as to the group's purpose.
Ultimately, protecting yourself from IP camera hacking requires a multi-faceted approach. You need to be aware of the risks, take proactive security measures, and stay vigilant for any signs of unauthorized access. By taking these steps, you can significantly reduce the risk of becoming a victim and safeguard your privacy and security.
Article Recommendations
- Remote Raspberry Pi Access The Ultimate Guide Troubleshooting
- Aditi Mistry News Photos More Hot Bigg Boss 18 Buzz

Detail Author:
- Name : Marilie McClure PhD
- Username : pfannerstill.jamie
- Email : raymundo62@bruen.com
- Birthdate : 1980-12-24
- Address : 97108 McClure Rest Rudolphberg, DE 43420-6890
- Phone : 812-208-5621
- Company : Gorczany-Daniel
- Job : Auditor
- Bio : Porro quia ut unde voluptatem ut rerum dolorem. Et veritatis iusto in expedita ea et. Debitis aut officia nostrum saepe nulla dolores. Est architecto non ex impedit aperiam voluptas ipsum sequi.
Socials
facebook:
- url : https://facebook.com/thelma.morissette
- username : thelma.morissette
- bio : Deleniti eum tempore impedit cum. Minus est saepe labore molestiae similique.
- followers : 1833
- following : 1155
twitter:
- url : https://twitter.com/thelma_dev
- username : thelma_dev
- bio : Est hic laboriosam molestiae et magni ex. Tempore voluptatem iste deserunt quae neque. Et unde quae eum ex quos minima.
- followers : 3256
- following : 967
tiktok:
- url : https://tiktok.com/@morissette1986
- username : morissette1986
- bio : Iusto fugit assumenda fugiat omnis ducimus reprehenderit architecto.
- followers : 5538
- following : 2994
instagram:
- url : https://instagram.com/tmorissette
- username : tmorissette
- bio : Placeat id sed corporis fuga impedit. Sit vero architecto deserunt praesentium quos necessitatibus.
- followers : 6109
- following : 1552