SSH Key Management: Best Practices & Security Tips [Guide]
Are your organization's digital keys left unguarded, creating unseen pathways for cyber threats? Ignoring robust SSH key management is akin to leaving the front door of your digital fortress wide open.
The stakes are incredibly high in today's interconnected world. SSH, or Secure Shell, keys provide a secure method for accessing systems remotely. IT teams worldwide depend on them every day for system administration, maintenance, support, and secure file transfers. However, this ubiquitous use also makes them a prime target for malicious actors. Poorly managed SSH keys can quickly become a nightmare, paving the way for unauthorized access, crippling data breaches, and a host of compliance violations that could sink an organization.
| Topic | Description |
|---|---|
| SSH Key Management | The systematic approach to generating, storing, using, rotating, and revoking SSH keys to ensure secure access to systems and networks. This involves implementing policies and procedures for key lifecycle management, access control, and monitoring. |
| Benefits of Effective SSH Key Management | Enhanced security posture, reduced risk of unauthorized access and data breaches, improved compliance with industry regulations (e.g., PCI DSS, HIPAA), streamlined access control, and increased operational efficiency. |
| Risks of Poor SSH Key Management | Unauthorized access to critical systems and data, data breaches, compliance violations, system downtime, reputational damage, and financial losses. |
| Key Components of SSH Key Management | Key generation, key storage (secure vaults), access control policies, key rotation, key revocation, key discovery, key auditing, and automation tools. |
| Common SSH Key Management Challenges | SSH key sprawl (proliferation of keys), lack of visibility and control over keys, weak key security practices, manual processes, and lack of automation. |
| Best Practices for SSH Key Management | Key discovery and inventory, centralized key management, strong key generation, secure key storage, access control policies, key rotation, key revocation, key auditing, and automation. |
| Key Discovery and Inventory | Identifying and cataloging all existing SSH keys in an environment to gain visibility and control over the SSH key landscape. |
| Centralized Key Management | Managing SSH keys from a central repository to enforce consistent policies and procedures across the organization. |
| Strong Key Generation | Using strong encryption algorithms and key lengths to generate SSH keys to prevent brute-force attacks. Common algorithms include RSA and ECDSA with key lengths of 2048 bits or more for RSA keys. |
| Secure Key Storage | Storing SSH keys in secure vaults with access controls to prevent unauthorized access. |
| Access Control Policies | Implementing access control policies to restrict access to SSH keys based on the principle of least privilege. |
| Key Rotation | Regularly rotating SSH keys to reduce the risk of compromise. |
| Key Revocation | Revoking SSH keys when they are no longer needed or when they are suspected of being compromised. |
| Key Auditing | Regularly auditing SSH keys to ensure compliance with security policies and procedures. |
| Automation | Automating SSH key management tasks to improve efficiency and reduce the risk of human error. |
| Tools for SSH Key Management | OpenSSH certificates, enterprise SSH key management solutions (e.g., HashiCorp Vault, CyberArk), and scripting tools. |
| OpenSSH Certificates | A mechanism for signing SSH keys to simplify key management and improve security. |
| Enterprise SSH Key Management Solutions | Dedicated tools for managing SSH keys at scale, providing features such as key discovery, centralized management, access control, and auditing. |
| Related Resources | NIST Special Publication 800-53, PCI DSS, HIPAA, and other industry regulations and guidelines. |
| External Resources | Example SSH Key Management Guide (Replace with a real, authoritative link) |
So, how exactly do you fortify your defenses and ensure your digital keys don't fall into the wrong hands? The answer lies in implementing comprehensive SSH key management strategies. It's not merely about generating keys; it's about their entire lifecycle from creation and storage to distribution, rotation, and eventual revocation.
- Troubleshooting No Results Youtube Channel Intro Leaked Video
- Aditi Mistry News Photos More Latest Updates
A proper plan starts with a comprehensive SSH key audit. This involves identifying all existing SSH keys within your environment. Think of it as a digital treasure hunt, but instead of gold, you're searching for potentially vulnerable access points. Discovery is paramount. You can't secure what you don't know exists. A first step in eliminating SSH key sprawl and properly assessing SSH security risk is to discover and inventory all SSH keys, and then to reign in centralized control of all keys.
Once discovered, you need to bring these keys under active management. This means moving away from ad-hoc practices and implementing a centralized system for key storage, access control, and monitoring. Centralized control is essential to prevent "key sprawl," a situation where SSH keys are scattered across numerous systems, making them difficult to track and manage.
Generating strong keys is crucial for the integrity of your SSH security. Always opt for strong encryption algorithms and robust key lengths. Common algorithms include RSA and ECDSA, with key lengths of 2048 bits or more for RSA keys. Weak keys are easily compromised, rendering all other security measures virtually useless.
- Aditi Mistry Career Social Media Public Image Update
- Mary Burke Leaks Explore Nudes Viral Content 2024 Trends
Consider Ubuntu systems. Implementing essential SSH key management best practices for Ubuntu systems, including generation, protection, rotation, and backup strategies, is paramount for maintaining secure and efficient server access. Comprehensive SSH key management best practices for Ubuntu systems should be adopted. Learn proper key generation, protection, rotation, and backup strategies to enhance your security posture.
Implementing namespaces within SSH key management can also improve security. To implement these best practices, you'll need to integrate namespace considerations into your SSH key management strategy. Namespaces create logical divisions within your key infrastructure, making it easier to manage access control and isolate sensitive resources.
Now, let's delve into some concrete steps you can take to elevate your SSH key management game. Remember, consistency and vigilance are your strongest allies.
1. Establish a Centralized Key Repository: No more scattered keys across various servers and workstations. Consolidate your SSH keys into a secure, centralized repository. This repository should enforce access controls and provide detailed audit trails, allowing you to track who accessed which keys and when.
2. Implement Role-Based Access Control (RBAC): Grant access to SSH keys based on user roles and responsibilities. This ensures that only authorized personnel can access sensitive systems and data. RBAC minimizes the risk of accidental or malicious misuse of SSH keys.
3. Automate Key Rotation: Regularly rotate your SSH keys to reduce the window of opportunity for attackers. Automate this process to minimize the administrative overhead and ensure that keys are rotated consistently. Consider rotating keys used for critical operations like signing particularly often.
4. Enforce Strong Key Generation Policies: Mandate the use of strong encryption algorithms and key lengths for all SSH keys. Provide users with clear instructions on how to generate secure keys and enforce these policies through automated checks.
5. Monitor Key Usage: Continuously monitor the usage of SSH keys for suspicious activity. Look for unusual login patterns, attempts to access unauthorized resources, or other anomalies that could indicate a compromised key.
6. Revoke Keys Promptly: When an employee leaves the organization or changes roles, immediately revoke their SSH keys. This prevents former employees or individuals with outdated access privileges from accessing sensitive systems.
7. Secure Key Storage: Store SSH keys in encrypted vaults or hardware security modules (HSMs) to protect them from unauthorized access. Never store keys in plain text or in insecure locations.
8. Educate Users: Provide users with comprehensive training on SSH key security best practices. Instruct users on how to issue SSH key pairs, utilize encryption and authentication mechanisms, and reinforce most appropriate techniques on key protection. Emphasize the importance of protecting their private keys and avoiding common pitfalls.
9. Implement Multi-Factor Authentication (MFA): Add an extra layer of security by requiring users to authenticate with MFA when accessing SSH keys. This makes it much more difficult for attackers to compromise keys, even if they have stolen a password.
10. Regularly Audit Your SSH Key Infrastructure: Conduct regular audits of your SSH key infrastructure to identify potential vulnerabilities and ensure compliance with security policies. Use automated tools to scan for weak keys, orphaned keys, and other security issues.
Securing SSH access to your Linux systems is a critical step in maintaining a robust security posture. With SSH being the primary method for remote system administration, its essential to implement proper hardening techniques to protect against unauthorized access and potential attacks. In this comprehensive guide, well explore proven SSH hardening techniques that will significantly improve your security.
Its important to understand that effective SSH key management entailing discovery, inventory, automation, and policy control should become integral to your identity and access management (IAM) strategy for ensuring security and compliance. SSH key management is, essentially, the practice of managing those critical admin keys so that you know at all times who has access to what and when that access was granted.
While X.509 certificates rely on digital certificates and issuing bodies (certificate authorities) to sign private keys, SSH keys are not governed by any institution. They are created, circulated, and used within transacting partners and organizations, and can be managed without any external oversight. This autonomy makes them both powerful and potentially dangerous if not properly managed.
SSH keys must be carefully managed, as a lack of SSH key management (including visibility and policy control) can create significant vulnerabilities. A real solution requires addressing authorized keys, the often-overlooked linchpin of SSH security.
Organizations of all sizes must reckon with the unwieldiness of SSH key management. You can tackle some of these challenges by governing keys according to best practices, like inventorying keys, rotating keys at fixed intervals, and assigning one key per user. Although passwordless SSH is easier to use and usually more secure than using passwords, SSH key management requires proper planning.
Best practices for key management organizations is primarily intended to address the needs of system owners and managers. When a pipeline creates a secret by itself, ensure that the scripts or binaries involved adhere to best practices for secret generation. This includes generating, importing, and exporting SSH keys in a secure manner.
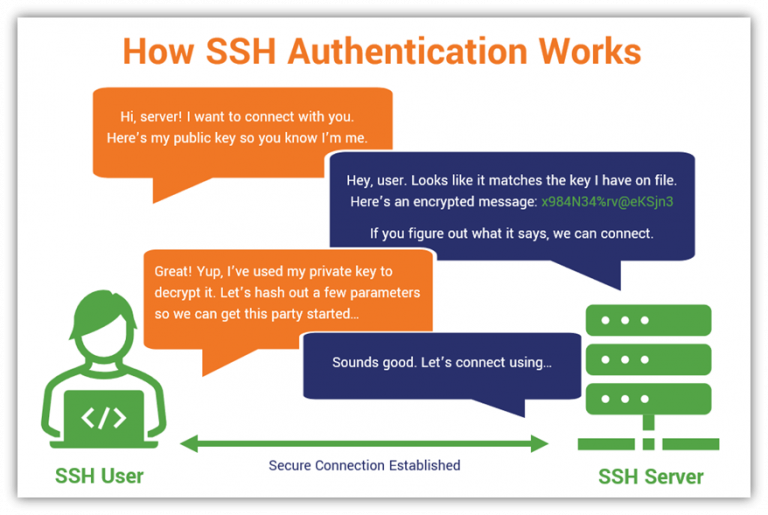
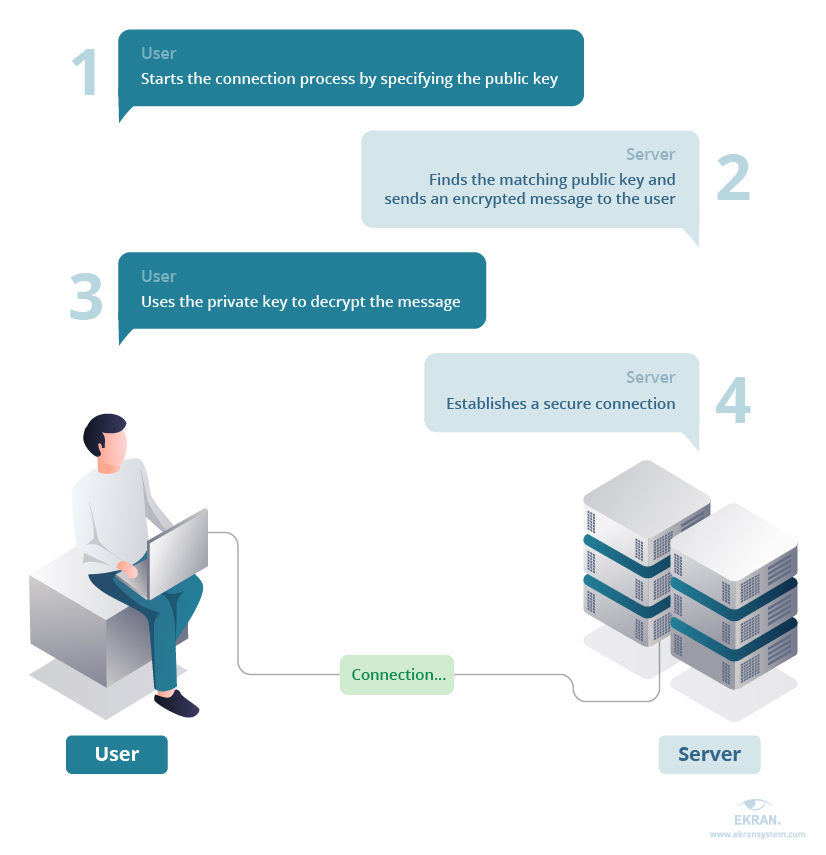
At the heart of secure SSH communication lies the power of cryptographic keys. SSH keys provide several benefits for protecting server access and data transmission. The public key and the private key are primary features of SSH.
This guide covers essential SSH key management best practices, including key generation, protection, rotation, and backup strategies. By implementing these recommendations, youll establish a robust security posture that balances convenience with strong protection of your sensitive systems and data. Learn how to use SSH key management best practices to protect your systems and network. So, without further ado, lets break down the SSH key management best practices you can put to work now to protect and manage access to your organizations IT environments and data. These best practices will be divided up into overarching categories that will help make things easy to follow.
Remember the importance of managing SSH keys. This is one way to prevent many such attacks. Identifying the requirements is the first step to implementing an SSH key management, according to the NIST report, security of interactive and automated access management using secure shell (SSH). Some of the recommended best practices are vital for your organizations safety. In todays distributed workplace model, privileged remote access to servers and systems is essential to ensure smooth operations. Secure shell (SSH) keys play a pivotal role in facilitating this access securely. IT teams worldwide use SSH keys daily for remote system administration, support and maintenance, and file transfers. Because SSH keys are so widely used, their proper management is essential. Best practices for SSH key management the process of properly managing SSH keys is very important to do correctly. You must ensure full coverage of your organizations keys and proper coverage of any security vulnerabilities. Properly managing SSH keys is crucial for maintaining a secure infrastructure. This article explores best practices for SSH key management, including the use of OpenSSH certificates, and reviews tools that can automate and enhance the process. Effective management of SSH keys is essential to prevent cyberattacks and maintain smooth operations. Poorly managed keys can lead to unauthorized access, data breaches, and compliance violations.
Ultimately, SSH key management is an access management issue that can best be tackled by core security teams. By taking a proactive approach to SSH key management, you can significantly reduce your organization's risk of cyberattacks and ensure the ongoing security of your critical systems and data.
Article Recommendations
Detail Author:
- Name : Vaughn Greenholt
- Username : nicolette.dooley
- Email : parker.wolf@brown.com
- Birthdate : 1971-05-02
- Address : 3555 Cody Cape Suite 648 East Michael, OK 28981-0864
- Phone : 669.434.3682
- Company : Champlin-Bernier
- Job : Construction Equipment Operator
- Bio : Quos occaecati nemo nisi nihil enim. Et explicabo quos facilis nihil. Perspiciatis odio praesentium autem expedita explicabo magni quia. Quis modi voluptatum ut quibusdam quisquam et sunt.
Socials
instagram:
- url : https://instagram.com/caylagibson
- username : caylagibson
- bio : Et harum ut aperiam ut qui qui voluptatem. At vero praesentium iusto nesciunt magnam earum.
- followers : 2660
- following : 1797
tiktok:
- url : https://tiktok.com/@cayla_gibson
- username : cayla_gibson
- bio : Officiis nihil quo dolore saepe quod et corrupti inventore.
- followers : 3205
- following : 2515
twitter:
- url : https://twitter.com/gibson1970
- username : gibson1970
- bio : Et qui sunt facere possimus qui praesentium. In velit et illum quasi adipisci. Totam aut rerum laborum.
- followers : 2811
- following : 177
linkedin:
- url : https://linkedin.com/in/cayla.gibson
- username : cayla.gibson
- bio : Facere provident ut non iste dicta qui nesciunt.
- followers : 2051
- following : 1374