Vietnam Camera Hack: Telegram Group Sells Private Footage!
Is your privacy truly your own? The unsettling reality is that countless private moments, captured by security cameras meant to protect us, are being illicitly accessed and sold on the dark corners of the internet, specifically targeting individuals and families in Vietnam. This is the chilling discovery that has sent ripples of concern throughout the digital security landscape.
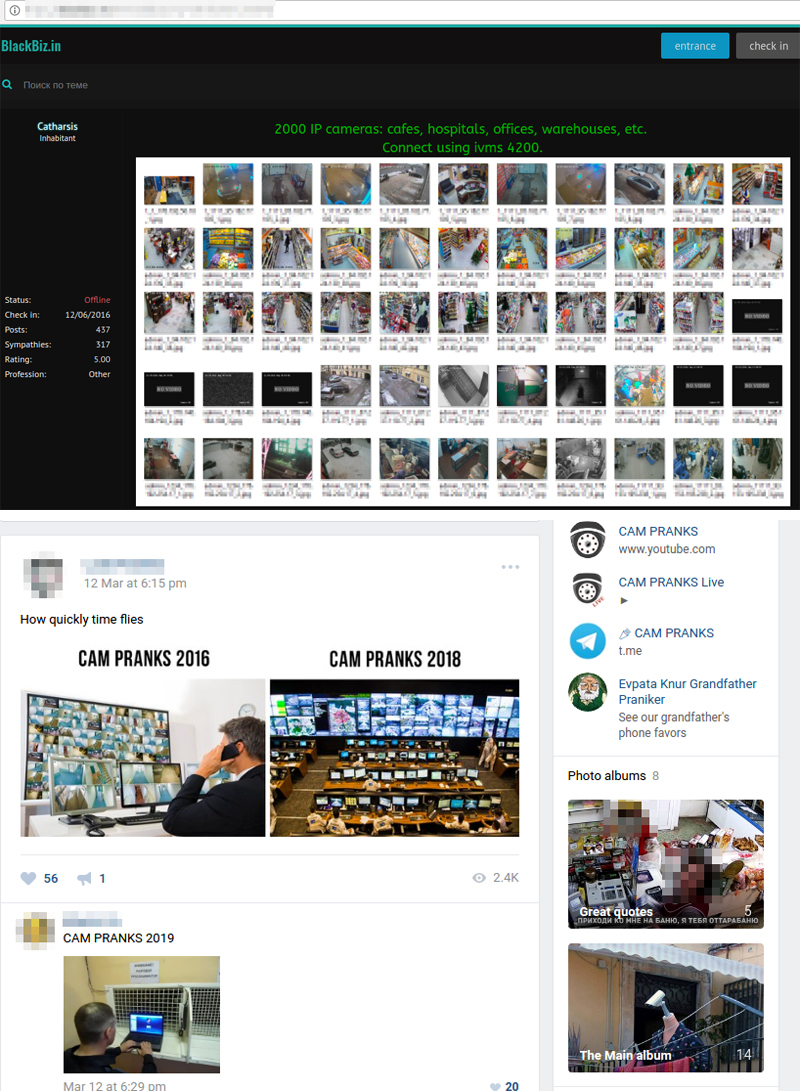
A disturbing revelation has come to light: a Telegram group engaged in the selling of private footage obtained from hacked security cameras. These cameras, surreptitiously placed in the most intimate settings bedrooms, dressing rooms, toilets, and spas across Vietnam have become sources of exploitation. The encrypted messaging platform Telegram has unwittingly become the marketplace for this illicit trade, exposing the vulnerabilities of even seemingly secure communication channels.
Researcher Minh Hung's investigation exposed the Telegram group, which brazenly identifies itself as specialized in hacking into private cameras installed in homes and businesses throughout Vietnam. The group extended an invitation to Hung to join their ranks, offering a glimpse into the disturbing content they peddle: "dark corners and hot scenes from families," as they described it. This blatant disregard for privacy and the law highlights the urgent need for increased vigilance and robust cybersecurity measures.
- Search Frustration Tips For No Results Found Issues
- Remembering Melanie Olmstead A Yellowstone Tribute Legacy
| Name | Minh Hung |
| Occupation | Cybersecurity Researcher |
| Area of Expertise | Network Security, Vulnerability Assessment, Digital Forensics |
| Notable Discovery | Exposing the Telegram group selling hacked camera footage in Vietnam. |
| Motivation | Driven by a desire to protect individual privacy and expose illegal online activities. |
| Impact | Raising awareness about the risks of unsecured IP cameras and the potential for privacy breaches. |
| Professional Affiliations | (Details may vary, but typically involved in cybersecurity research communities) |
| Contact Information | (Generally kept private for security reasons) |
| Website/Profile | LinkedIn (Example - actual profile may vary) |
The ease with which individuals can access and share such sensitive material is alarming. The Telegram group, identified by the handle @nhomhackcameras, openly invites users to "view and join right away." This accessibility underscores the urgent need for Telegram and other messaging platforms to strengthen their security protocols and actively combat the proliferation of illegal content on their services. The lure of voyeurism, coupled with the anonymity offered by encrypted platforms, creates a breeding ground for such exploitation.
The mechanics of accessing the illicit content are disturbingly simple: download the Telegram app, open the channel, and gain access to the hacked footage. This ease of access, coupled with the unofficial nature of the service, further contributes to the problem. It's a stark reminder that seemingly innocuous apps can be exploited for malicious purposes, and users must be vigilant about the content they consume and the platforms they trust.
The scope of the problem extends beyond a single Telegram group. Untold hours of private camera footage, captured from bedrooms, changing rooms, toilets, and massage parlors across Vietnam, have been hacked and put on sale online. This widespread exploitation suggests a systemic vulnerability in the security of IP cameras and the networks they are connected to. It's a wake-up call for consumers and businesses alike to prioritize cybersecurity and take proactive measures to protect their privacy.
The description of the private Telegram group that invited Minh Hung to join was chillingly straightforward: "A group specialized in hacking into private cameras of families and shops in Vietnam." This blatant admission of criminal activity highlights the brazen nature of these perpetrators and the urgent need for law enforcement to take swift and decisive action. The lack of fear of reprisal suggests a sense of impunity, which must be challenged and dismantled.
The issue extends beyond individual privacy breaches. An explosive report from IPVM, a respected surveillance industry trade publication, revealed that child sexual abuse material (CSAM) sourced from hundreds of hacked Hikvision cameras is being sold on Telegram. This disturbing finding underscores the potential for these breaches to be exploited for the most heinous of crimes, demanding immediate and comprehensive intervention. The presence of CSAM on these platforms necessitates a multi-faceted approach involving law enforcement, technology companies, and child protection organizations.
The accessibility of these illicit channels is a persistent threat. The message "If you have Telegram, you can view and join \ud83d\udd25 camera escondida / ipcam \ud83d\udd25 right away" serves as a constant reminder of the ease with which individuals can access this material. The use of emojis and suggestive language further lures unsuspecting users into these dark corners of the internet.
Adam, a tech journalist with over 20 years of experience, brings a wealth of knowledge to the discussion. His expertise spans a wide range of product categories, including timelapse cameras, home security cameras, NVR cameras, photography books, webcams, 3D printers and scanners, borescopes, radar detectors, and drones. His insights into the vulnerabilities of these devices are invaluable in understanding the scope of the problem and identifying potential solutions. Adam's comprehensive understanding of the technology landscape allows him to provide informed commentary on the security risks associated with interconnected devices.
The illicit trade is not confined to Telegram alone. Online platforms are rife with disturbing content. The phrase "Watch xxx hack camera ip em gai viet thu dam movies at pornma.com porn tube [32:19x392p]" demonstrates the brazen advertisement of sexually exploitive material obtained through hacking. The explicit nature of these advertisements highlights the pervasive nature of the problem and the challenges in regulating online content.
The promise of easy access is a common lure. The phrase "Devil ip cam qr hack \ud83d\udd24 \ud83d\udd24 \ud83d\udd24 \ud83d\udcf1 \u2139\ufe0f " followed by Arabic text offering "full subscription" and access to "3 important groups" for hacked camera access underscores the organized nature of this criminal enterprise. The use of QR codes and promotional offers suggests a sophisticated marketing strategy designed to attract and retain customers.
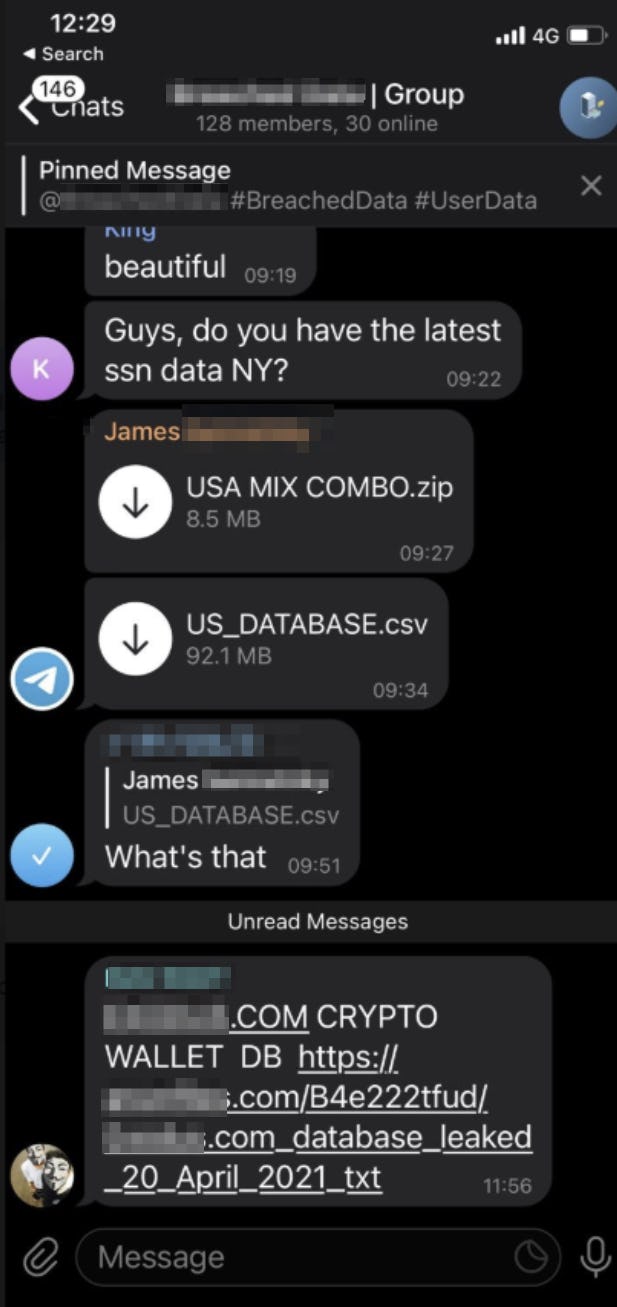
Further evidence of the organized nature of the hacking and distribution network is seen in the mention of "Qr codes | cam share | free cams | ipcams | hacked cams | home cameras | webcams | qrcodes | ivms | dahua | port8000 | pprt37777 146 members." This list of keywords and technical terms indicates a community of individuals actively involved in hacking and sharing camera feeds. The mention of specific ports (port8000, pprt37777) suggests a technical understanding of how IP cameras are accessed and exploited.
The existence of groups like "nh\u00f3m hack cam t\u00ecnh nh\u00e2n" further illustrates the targeted nature of these attacks. The Vietnamese phrase translates to "group hack love camera," suggesting a focus on hacking cameras used for romantic purposes or capturing intimate moments. This targeted approach highlights the depravity of the perpetrators and the vulnerability of individuals in their private lives.
The phrase "This is very much wip and basically is functional enough to work for my needs" suggests that some of these hacking tools and techniques are still under development. This ongoing evolution of hacking methods poses a constant challenge for cybersecurity professionals and highlights the need for continuous vigilance and innovation in security measures. The fact that these tools are "functional enough" even in their early stages is a testament to the ingenuity and persistence of the hackers.
The mention of "telegram bot code" and "whitelist handler" indicates the use of automated tools to identify and exploit vulnerable cameras. The phrase "detect.py does the detection from the camera streams and writes to an output folder" suggests a systematic process for scanning networks for vulnerable devices and extracting footage. This automation allows the hackers to scale their operations and target a larger number of victims.
The existence of groups like "hot \ud83d\udd25 hidden cam \ud83d\udcf9" further demonstrates the demand for this type of illicit content. The use of emojis and suggestive language is a common tactic to attract users and normalize the exploitation of private moments. The term "hidden cam" implies that the footage is obtained without the knowledge or consent of the individuals being recorded.
The Telegram group claims to specialize in hacking into "private cameras of families and shops in vietnam" and invited Hung to join them on the channel. This direct targeting of families and businesses underscores the indiscriminate nature of these attacks and the potential for widespread harm. The invitation to join the channel is a brazen attempt to recruit new members and expand the reach of the criminal enterprise.
Hackread.com has obtained screenshots that provide further evidence of the activities of these Telegram groups. These screenshots likely contain sensitive information, such as examples of the hacked footage, conversations between members, and details about the methods used to access the cameras. The publication of these screenshots serves to raise awareness about the problem and hold the perpetrators accountable.
The phrase "Unofficial service for telegram messenger" serves as a disclaimer, acknowledging that Telegram is not directly involved in these activities. However, it also highlights the platform's role in facilitating the illegal trade. Telegram has a responsibility to take proactive steps to identify and remove these groups and prevent the exploitation of its platform for criminal purposes.
The invitation to "Send message via telegram app" underscores the ease with which individuals can communicate and coordinate their activities on the platform. The anonymity offered by Telegram allows these criminals to operate with impunity, making it difficult for law enforcement to track them down.
The existence of groups like "Spy cam ip qr \ud83d\udcf8 3.2k members" further demonstrates the popularity of this type of content. The large number of members indicates a significant demand for hacked camera footage and the potential for substantial financial gain for the perpetrators.
IPVM's investigation uncovered numerous sales offers for nude videos on Telegram, including footage from cameras labeled for "family homes, medical offices, salons, locker rooms." This targeting of sensitive locations underscores the vulnerability of individuals in their private lives and the potential for significant emotional distress. The fact that these cameras are labeled suggests that the hackers have a detailed understanding of the locations and activities being recorded.
IPVM also found messages in Telegram channels that advertise access to hacked cameras using terms like "cp" (child porn), "kids room," "family room," and "bedroom of a young girl." This disturbing finding underscores the potential for these breaches to be exploited for the most heinous of crimes, demanding immediate and comprehensive intervention. The use of these terms is a clear indication of the perpetrators' intent to target vulnerable individuals and exploit them for their own gratification.
Hung gained access to 15 cameras in the bedrooms, living rooms, and dressing rooms of clothing shops and spas. This unauthorized access highlights the vulnerability of businesses and the potential for significant reputational damage. The fact that Hung was able to gain access to so many cameras underscores the lack of security measures in place and the urgent need for businesses to prioritize cybersecurity.
When Hung selected camera footage from a family's bedroom, he saw that the timestamps shown on the footage matched the actual time and date. This confirmation of the authenticity of the footage underscores the severity of the breach and the potential for significant harm to the victims. The accurate timestamps also provide valuable evidence for law enforcement in their investigations.
Hung became worried because his family has cameras installed as well. This personal connection to the issue underscores the universal vulnerability to these types of attacks. Anyone who uses IP cameras is potentially at risk, and it is essential to take proactive steps to protect one's privacy.
The term "* ip cam mom korean ipcam telegram" is a keyword phrase that likely reflects common search terms used by individuals seeking access to this type of illicit content. The inclusion of "mom" and "korean" suggests a focus on specific demographics and types of footage. The use of these keywords highlights the need for targeted interventions to combat the spread of this material.
Article Recommendations
- Gabby Beans Rising Star Her Life Career Tv Shows
- Joyce Dewitts Net Worth From Threes Company To Millions
Detail Author:
- Name : Ms. Yessenia Wilkinson
- Username : eli.thompson
- Email : lowell.abshire@satterfield.com
- Birthdate : 1970-05-20
- Address : 93100 Ruby Plains New Lurlineport, NE 21800
- Phone : (970) 819-4470
- Company : McClure Inc
- Job : Substation Maintenance
- Bio : Molestiae non quasi nihil quo ut. Dolor sed nihil officiis et. Ad non culpa ea necessitatibus. Corrupti eius hic rerum aut est maiores illo.
Socials
linkedin:
- url : https://linkedin.com/in/cyrilhickle
- username : cyrilhickle
- bio : Sed cupiditate deleniti eius earum.
- followers : 4050
- following : 2897
facebook:
- url : https://facebook.com/cyrilhickle
- username : cyrilhickle
- bio : Voluptatem dolor dolorum dolores est consequatur iure.
- followers : 5252
- following : 2364