Apple Remote Desktop Guide: Control Your Mac From Anywhere!
Ever wished you could be in two places at once, effortlessly managing multiple computers from the comfort of your own Mac? The power to remotely control other computers, transfer files seamlessly, automate tedious tasks, and generate comprehensive reports is now within your reach, all thanks to Apple Remote Desktop.
Apple Remote Desktop offers a robust suite of tools designed to streamline your workflow and boost productivity. Imagine the ability to troubleshoot a colleague's Mac across the office or access your home computer while traveling, all without leaving your current workstation. It's not just about convenience; it's about efficiency and control.
| Feature | Description |
|---|---|
| Remote Control | Access and control other Macs on your network. |
| File Transfer | Securely copy files between your Mac and remote computers. |
| Task Automation | Automate repetitive tasks with built-in tools. |
| Reporting | Generate reports on software and hardware inventory. |
Mastering Apple Remote Desktop unlocks a new dimension of possibilities for Mac users. It empowers you to provide remote support, manage systems efficiently, and collaborate seamlessly with others. The benefits extend beyond individual users, offering significant advantages to IT professionals and businesses of all sizes.
However, the landscape of remote access has evolved. macOS Catalina (10.15) introduced heightened security features that necessitate additional permissions for certain remote support applications like GoToAssist Remote Support v5 to function at their full potential. Navigating these security protocols is crucial to ensure seamless and secure remote control.
For IT professionals supporting macOS Catalina or later, guiding your customers through the permission granting process is paramount. Clear and concise instructions are key to enabling the necessary access for effective remote troubleshooting and support. Here's a typical procedure you might instruct your customer to follow:
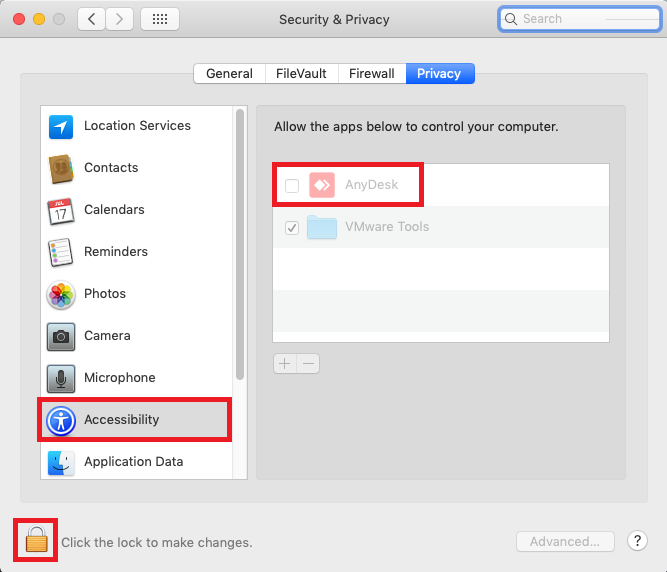
1. Navigate to System Preferences, then click on Security & Privacy.
- Search Empty Tips Tricks When You Find No Results
- Park Shin Hyes Next Project News Charity Rumors More
2. Select the Privacy tab.
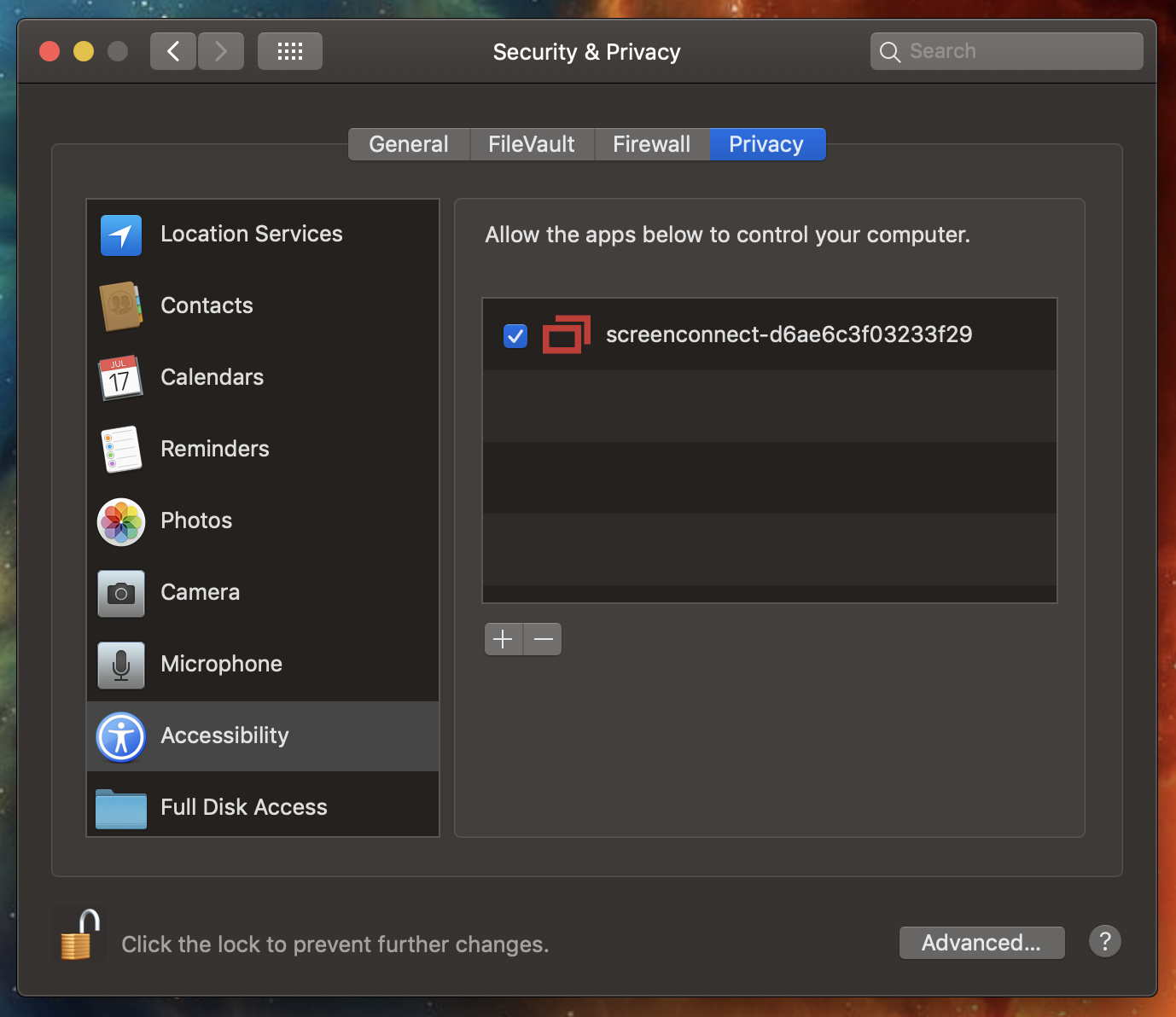
3. In the left-hand sidebar, choose Accessibility, Screen Recording, and Full Disk Access.
4. Click the lock icon in the lower-left corner to make changes.
5. Enter your administrator password.
6. Check the box next to the application requiring permission (e.g., GoToAssist).
7. Click the lock icon again to save your changes.
These steps ensure that the remote support application has the necessary permissions to control the screen, access files, and interact with the system. Without these permissions, functionality may be limited, hindering the effectiveness of remote support sessions.
The core value of remote support lies in the ability to directly interact with a user's desktop, mirroring their screen to diagnose issues firsthand. This visual connection facilitates quicker problem identification and resolution, significantly reducing downtime and frustration. Live chat features further enhance the support experience, allowing for real-time communication and clarification of problems.
Modern remote support solutions go beyond simple screen sharing and chat. Features like predefined replies save valuable time by allowing technicians to quickly respond to common queries. The ability to push URLs directly from the technician's device to the user's browser streamlines the process of directing users to relevant resources or troubleshooting steps.
One often overlooked challenge in remote access is keyboard compatibility. Windows and Mac devices employ different keyboard configurations, leading to inconsistencies in shortcut mappings. Many remote applications fail to adequately address this disparity, forcing users to adapt to unfamiliar keyboard layouts. However, solutions like keyboard mapping bridge this gap, enabling users to seamlessly employ their preferred Mac keyboard combinations and shortcuts even when controlling a Windows PC.
The decision to adopt a remote support solution often hinges on its ability to support macOS devices. As the prevalence of Macs in the workplace continues to rise, organizations need tools that can effectively manage and support these systems. A robust macOS support capability was a critical factor for many when selecting a remote support platform. They sought a solution that provided comprehensive support for these devices, ensuring seamless operation and minimizing potential disruptions.
For those seeking alternative remote desktop solutions, Chrome Remote Desktop offers a compelling option. It leverages the latest web technologies to connect users to their devices, regardless of their location. Whether you need to access your work computer from home, retrieve a file from your home computer while traveling, or collaborate with friends or colleagues, Chrome Remote Desktop provides a secure and reliable connection.
To get started with Chrome Remote Desktop, visit the Chrome Remote Desktop site and click on "Remote Support" near the top. Follow the prompts to download and install the Chrome Remote Desktop extension from the Chrome Web Store. Once installed, you can easily set up remote access to your computer and connect to other devices.
Consider an IT team of five individuals tasked with supporting nearly 200 Apple devices and 600 Windows machines. For such a team, a remote capability integrated directly into their systems is indispensable. The ability to remotely access and troubleshoot devices saves countless hours of manual intervention and ensures rapid resolution of issues. Furthermore, single sign-on (SSO) integration streamlines the user experience by reducing the number of passwords users need to remember, enhancing both security and convenience.
Splashtop Remote Support emerges as a critical tool for managed service providers (MSPs) and IT professionals demanding a dependable, secure, and comprehensive remote support solution for Mac devices. Its unique blend of unattended access, scalable management features, proactive monitoring capabilities, and robust security protocols positions it as an invaluable asset for any organization striving to optimize its IT support operations.
The power of unattended access cannot be overstated. It allows IT professionals to access and manage devices even when no one is physically present at the remote location. This is particularly useful for performing maintenance tasks, installing updates, and troubleshooting issues outside of normal business hours, minimizing disruption to end-users.
Scalable management capabilities are essential for organizations with a large number of devices to manage. A robust remote support solution should provide centralized management tools that enable IT professionals to easily deploy software, configure settings, and monitor the health of all devices from a single console. This streamlines the management process and ensures consistency across the entire organization.
Proactive monitoring allows IT professionals to identify and resolve issues before they impact end-users. A comprehensive remote support solution should provide real-time monitoring of system performance, security alerts, and other critical metrics. This enables IT professionals to proactively address potential problems and prevent them from escalating into major incidents.
Security is paramount when it comes to remote access. A reliable remote support solution should employ robust security protocols to protect sensitive data and prevent unauthorized access. This includes features like end-to-end encryption, multi-factor authentication, and granular access controls.
For those seeking to directly configure remote access on a Mac, the built-in sharing settings offer a straightforward approach. To access these settings, navigate to the Apple menu, select "System Settings," click on "General" in the sidebar, and then click on "Sharing." You may need to scroll down to find the Sharing option. The system preferences provide a direct route to configuration; the interface is quite intuitive.
Within the Sharing settings, you'll find options for "Remote Management" and "Remote Login." Remote Management allows you to control the screen of your Mac from another computer on the network, while Remote Login enables you to access your Mac using SSH (Secure Shell) from a remote location.
If you intend to grant remote users full access to the disk on your Mac, you can enable the "Allow full disk access for remote users" option. However, exercise caution when enabling this option, as it grants unrestricted access to your entire file system. Only enable this option if you fully trust the remote users who will be accessing your Mac.
LogMeIn for Mac stands out as a powerful remote desktop application catering to Mac users of all skill levels and requirements. Its versatility makes it suitable for individuals, small businesses, IT professionals, and help desk technicians alike. LogMeIn offers specialized tools tailored to each of these user groups, positioning it as a leading contender in the enterprise remote desktop support market.
The diverse features of LogMeIn for Mac address a wide range of remote access needs. Individuals can use it to access their home computer from work or vice versa, while small businesses can leverage it to provide remote support to their employees. IT professionals can use it to manage and maintain remote servers, while help desk technicians can use it to troubleshoot user issues remotely. The tool's adaptability to varied enterprise requirements contributes to its prominence in the field.
While searching for solutions it is important to always double check the spelling or type a new query if you did not find the desired result.
Article Recommendations
- Martin Eve Kretz Divorce Fact Vs Fiction Search Tips
- Discover Melanies Story From Search Errors To Inspiring Life

Detail Author:
- Name : Marques Powlowski
- Username : pat00
- Email : dstamm@yahoo.com
- Birthdate : 1991-04-18
- Address : 54226 Jaylon Shoal Litzyburgh, VT 58043-0149
- Phone : +1.910.801.3244
- Company : Pfeffer-Reilly
- Job : Database Manager
- Bio : Deleniti odit rem sunt. Earum quia at aspernatur dolore harum expedita.
Socials
tiktok:
- url : https://tiktok.com/@schinner1972
- username : schinner1972
- bio : Quia nesciunt dicta non consequatur cupiditate. Sit quia ut error vel.
- followers : 4797
- following : 1117
linkedin:
- url : https://linkedin.com/in/jacyntheschinner
- username : jacyntheschinner
- bio : Dolorem ut suscipit natus officiis itaque.
- followers : 5354
- following : 2433